
Welcome to the cutting-edge world of DevSecOps 2.0, where development, Security, and operations meet to tackle modern cyber threats. Yes! Protecting your business from cyberattacks is an indispensable step for you as a business owner.
In this dynamic digital realm, safeguarding from third-party attacks is crucial. For this reason, there are plenty of applications and software available that protect systems against malware and other vulnerable attacks.
Introduction
DevSecOps 2.0 is an advanced approach to software development that integrates security practises throughout the entire development process. It is a crucial and highly prioritized evolution that aims to enhance security during the development process. The SDLC (Software Development Life Cycle) encompasses everything from the initial planning phase to the final deployment stage.
In this post, we shall discuss an intricate web of advanced security integration to elevate the development.
Get ready to explore some of the interesting features of DevSecOps 2.0, such as role, components, comparison, integration, and further detail.
Without delay, let’s get started!
1. DevSecOps 2.0 – An Outline
There are people who may be aware of this security integration; however, some will be hearing about DevSecOps 2.0 for the first time. Whether you’re hearing the word for the first time or are aware of it, this section is exclusively for you all guys. Don’t miss it.
Dev stands for development, where Sec is for Security, and Ops is for operations, which is an extended DevOps method.
DevSecOps 2.0 is a holistic practice that ensures Security at every stage of the software development lifecycle. As everyone knows, prevention is better than cure; similarly, it emphasizes proactive measures.
The collaborative measures implemented at every stage of development set it apart from others in comparison. Furthermore, it advocates for a security system that fosters shared responsibility in software development.
In a word, DevSecOps 2.0 is the best approach to enhance overall security in complex digital cyber threats.
2. Significance Of DevSecOps 2.0
DevSecOps 2.0 holds some significant vital features that are crucial to adapt during SDLC phases. They are,
➤ Shift-Left Security
DevSecOps 2.0 encourages the shift-left approach to enhance the Security of the final product and enables feedback after every stage of the lifecycle. Thus, it encourages collaboration and reduces vulnerabilities.
Also Read: Node.js Security Practices: Building a Fortified Web App
➤ Risk Mitigation
In general, risk mitigation is a planning stage that every business prepares to lessen threats and data leaks. DevSecOps 2.0 addresses third-party attacks as soon as it identifies them. Thus, it prevents costly security breaches and enhances the overall Security before, during, and after deployment.
➤ Competitive Advantage
The most significant reason to opt for DevSecOps 2.0, well-versed security automation, is a competitive advantage. Yes, every developer team or organization would love to withstand others in every field, whether it be software development or project management.
In that instance, businesses prefer using it to enhance Security, quality of products, customer satisfaction, and other potential reasons.
➤ Cross-Functional Skill Development
Another reason is for their integration and collaboration. DevSecOps 2.0 encourages the cross-functional skills of the developers and helps them gain knowledge about security breaches.
These are some of the significant reasons to choose DevSecOps 2.0 for your Software Development Lifecycle journey.
3. Role Of DevSecOps 2.0 In The Development World
We hope that you might have achieved some idea on DevSecOps 2.0 from the above-discussed things. Now, let’s explore the role in simple points!
● Early Integration
● Collaboration
● Security Automation
● Provides Continuous Improvement
● Real-Time Feedback
● Agility And Faster Results
● Cost-Efficiency
● Compliance And Auditing
● Offers Sustainability For Software Throughout Span
4. Components Of DevSecOps 2.0
These are some significant components in the DevSecOps 2.0 approach that include code analysis, change management, compliance management, threat modeling, and security training.
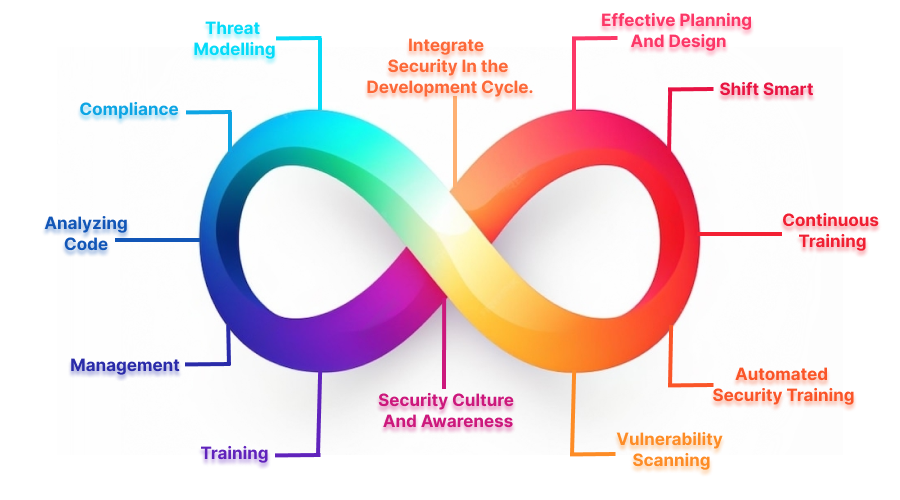
➤ Analyzing Code
It is to investigate the source code of the application to ensure it is out of cyber attacks and enhance the quality of the code.
➤ Management
Changing the software management tools to keep track of, analyze, and report the requirement changes helps to prevent vulnerabilities.
Other Tools: Top RevOps Software Tools: Reformation for your Business
➤ Compliance
Regulatory compliance management is an ongoing process that ensures the system complies with the security standards and corporate policies & requirements.
➤ Threat Modelling
It is a process that takes place before and after application updates. DevSecOps 2.0 team examines the security threats and fixes them accurately to avoid further breaches.
➤ Training
It is nothing but training the developers to adapt to the latest version of the security guidelines to enhance their knowledge of cyber attacks and deploying the applications. By ensuring this, both development and operation teams incorporate independent decisions while developing and deploying the application.
➤ Integrate Security In the Development Cycle.
Well, from the above-mentioned points, you can make a decision that DevSecOps 2.0 is more beneficial for building efficient software. So, integrating it into your development cycle is necessary. But how will you do it? What you ought to do? Read ahead to know all that…
➤ Security Culture And Awareness
Train every member of each team to make them understand the significance of Security.
➤ Effective Planning And Design
Prioritize the security considerations from the first phase of the SDLC. As everyone knows, planning projects with effective workflow models makes developers work faster. If they opt for this method, then it elevates the project flow even faster.
➤ Continuous Training
Provide ongoing support to every team member and make them aware of every nuke and corner of the security breaches. Teach them about the best practices to enhance the end-product results.
➤ Shift Smart
Smart Shift is a software development approach that places a strong emphasis on security and encourages collaboration among development, security, and operations teams.
The process entails incorporating security measures at every stage of the software development lifecycle, starting from the design phase and continuing through deployment. This is achieved through the use of automation and various tools.
In DevSecOps 2.0, the shift right practice involves testing performance and quality under real-world conditions.
Shift left is based on the initial stages of the software development life cycle and the efforts of the team that follows organisational collaboration between the developer, Security, and operations.
➤ Automated Security Training
Try to implement security testing tools and integrate them into the CI/CD pipeline. Moreover, you can utilize the testing phases like dynamic application security testing (DAST) and interactive application security testing (IAST). Don’t worry, you will get to know about them in the upcoming sections.
➤ Vulnerability Scanning
This is the stage where developers utilize software testing tools like SCA software composition analysis to scan and ensure that there are no vulnerable attacks in open-source components.
Also Read: Effective Tips for Software Testing
5. Difference Between DevSecOps 2.0 And SecOps
So far, you have explored the DevSecOps 2.0 and got an idea about its features and significance. But do you know there is another approach? Yes, similar to it, SecOps is also a method that provides Security for the software.
However, why is it not as popular as DevSecOps 2.0? Have you ever heard about it? Let’s take a look at them in this section.
Both approaches concentrate on enhancing the security systems with notable differences in methods and goals.
➤ DevSecOps 2.0
It integrates Security directly into three stages, which include development, Security, and operation.
DevSecOps 2.0 provides an automation-centric approach to check every fundamental aspect, like code analysis, compliance checks, and security testing.
This approach provides proactive Security and ensures the prevention of security vulnerabilities at every phase, from planning to deployment.
➤ SecOps
It is known for its post-deployment check, unlike DevSecOps 2.0, which only provides the security check after or during the product delivery.
This approach also offers continuous monitoring but does not resolve potential security issues as effectively as DevSecOps 2.0.
SecOps relies on the security tooling SIEM to detect systems and respond to security events.
These are some of the significant differences between DevSecOps 2.0 and SecOps.
6. What Challenges Does DevSecOps Address?
Although security is crucial, it is often given less priority and considered towards the end of programme development. It is crucial for companies to prioritise security in order to establish consumer trust in apps. DevSecOps is a solution that addresses the following issues:
➤ speed
Adding security during production and distribution would make the process more efficient and risk-free. DevSecOps facilitates the rapid release of new apps that meet or exceed business requirements.
➤ Improved Security
Software security concerns that breach consumer data can lead to businesses being subjected to legal action and experiencing damage to their brand image. The implementation of DevSecOps Automation prioritises security, ensuring that developers consistently include application security considerations into their development processes.
➤ Enhanced Software Efficiency
The early integration of security measures with software development lifecycle tools facilitates the implementation of registry image scanning, digital signature, and code analysis, hence ensuring the integrity of the code and mitigating potential financial ramifications.
7. How Adapting To The DevSecOps 2.0 is beneficial?
DevSecOps 2.0 provides enormous benefits on two sides, both developers and clients or users. Buckle up. Let’s explore them one by one!
➤ From Developer Side
From previous sections, you can conclude that DevSecOps 2.0 assists developers from the planning to the deploying stage. On the whole, it offers these benefits to them.
➤ Faster Development
Developing and deploying software is not a simple thing; it consumes a lot of effort and new surveys from stage one. Security check automation reduces the burden of developers and allows them to concentrate on the coding part.
➤ Enhanced Collaboration
As the name DevSecOps 2.0 mentions, it improves the transparency between three teams, which results in enhanced collaboration and smooth workflow.
➤ Better Code Quality
Security automation consistently addresses third-party attacks and generates feedback. It allows developers to write efficient codes to deploy high-quality software.
➤ Adaptability
DevSecOps 2.0 paves the way to encounter evolving cyber-attacks that assist developers in adapting to the best practices. For Customers.
DevSecOps 2.0 not only enhances the streamline of workflow but also offers various benefits to the clients or users. It’s time to take a glance at it!
➤ User Privacy
It protects the customer data and makes their software trustworthy. Moreover, enhancing user privacy builds trust in the developing organization or development team. Thus, DevSecOps 2.0 also elevates the credibility of a Company.
➤ Quality Assurance
Deploying cutting-edge software or applications with assured quality is not easy; however, DevSecOps 2.0 simplifies it.
➤ Risk Reduction
DevSecOps 2.0 significant aim is to enhance the overall Security of cyber threats and reduce vulnerability risks with proactive measures. In that instance, this approach in the SDLC elevates and assures risk-free software.
➤ Cost Efficiency
The first thing in every client’s mind will be the budget of the software. Thus, DevSecOps 2.0 collaboration and security check features reduce the burden of the developers and make it cost-efficient.
➤ Customer Satisfaction
Guess what? If you’re about to enjoy the entire advantages of every software or application, then surely, you would be satisfied. Isn’t it? Yes! Just by putting yourself in the shoes of clients or users, you can sense the exact feel.
8. DevSecOps 2.0 Tools
Harnessing the power of tools in this digital world to enhance any progress is highly beneficial. Similarly, DevSecOps 2.0 tools assist in examining the flaws in every phase and ensure the developers deploy high-quality end products.
DevSecOps 2.0 uses some exclusive testing tools to identify the vulnerabilities during the development process. It includes,
● SAST
● SCA
● IAST
● DAST
➤ Static Application Security Testing – SAST
There are some specific SAST tools available to check modern cyber-attacks in proprietary source code. Such as,
- Klockwork
- SpectralOps
- Checkmarx
- Veracode
- LGTM.COM
- Reshift
- INSIDER CLI
- Codacy
- HCL AppScan
- Jit
- Teller
➤ Software Composition Analysis – SCA
It’s an automation visibility process to know the purpose of risk management, license compliance, and Security in open-source software. To perform this analysis, plenty of tools are available; they are,
- GitHub
- Wiz
- Snyk
- GitLab
- Microsoft Defender For Cloud
- Men.io (WhiteSource formerly)
- Black Duck Software Composition Analysis
- Constant Security
- CAST Highlight
- SOOS SCA + DAST
- JFrog Software Supply Chain Platform
➤Interactive Application Security Testing – IAST
In this testing process, the software is tested in the production environment, i.e., outside perspective. It gives real-time analysis results that help to extend features and enhance performance. Make the testing more efficient with these exclusive tools, like,
- Synopsys
- Fortify Software
- Burp Suite
- Qualys
- Security AppScan
- SonarSource
- Semgroup
- Micro Focus
- Veracode
- Checkmarx
- Netspaker
➤ Dynamic Application Security Testing – DAST
Last but not least, it is also a tool to test the cyber-attacks that arise from the outside network. These tools perform similar actions to the hackers; in simple words, it can be mentioned as self-hack testing.
- Astra Penstest
- Invicti (Netsparker Formerly)
- Indusface WAS
- Acunetix
- Intruder
- PortSwigger
- Detectify
- AppCheck Ltd
- Hdiv security
- Rapid7
- MisterScanner
Embrace the power of security check tools to get good outcomes using DevSecOps 2.0 and make clients and developers happy. In addition, these tools work on various platforms and are mostly similar in patterns but differ in approach. Learn deeply about them to gain sufficient knowledge to access them perfectly.
Take your software development process to new heights and outshine your competitors by implementing DevSecOps 2.0, an advanced approach to software development.
Wrapping it up…
So, there you have it: DevSecOps 2.0: A Deep Dive Into Advanced Security Integration. Hopefully, this article has been informative for you and gives you an elaborate view of integrating Security in development. Cyber threats can be damaging to any business as most of their customers’ data is out there online. Utilizing a practical approach, such as DevSecOps 2.0, across the developing stage can help you stay safe from cyber threats.
Use the available tools to delve deeper into the world of cyber-attacks in order to effectively address them and improve your approach. Experts recommend prioritizing the adoption of DevSecOps 2.0 to enhance the development and deployment process of software or applications. Embrace this approach to STAND OUT!






