Businesses, large and small, operate within a complex landscape of online threats. From data breaches to brand infringement, protecting your company’s sensitive information is paramount. Proxies can be a valuable tool in your cybersecurity arsenal, offering an extra layer of defense for your online data.
But how exactly can proxies enhance your business’s security posture? Here are some key benefits and strategies for leveraging proxies effectively:
Understand the Basics of Proxies
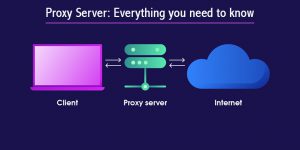
Before considering any strategy and exploring resources like Proxy.Coupons for deals, let’s get a grip on what proxies are and how they work. A proxy server acts as a gateway between your business and the internet. When your team accesses online resources, the requests first go through the proxy. This setup adds an extra layer of security, as your real IP address remains hidden. Proxies also offer other benefits, such as content filtering and improved network performance.
Choose the Right Type of Proxy
Not all proxies are created equal. Different types cater to specific needs. Here’s a brief overview:
- Datacenter Proxies: Ideal for general web browsing and basic anonymity.
- Residential Proxies: Offer the highest level of anonymity, mimicking real user traffic patterns.
- Mobile Proxies: Simulate traffic from mobile devices, valuable for mobile app testing and market research.
Consider your specific requirements and security priorities when selecting a proxy solution. Reliable proxy providers offer various plans and features to suit your business’s needs.
Regularly Update and Maintain Your Proxy Server
Like any other piece of technology, proxy servers need regular updates and maintenance. Outdated software can become a vulnerability, opening up your system to potential cyber threats. Set a schedule for regular updates and stick to it. Additionally, perform routine checks to spot and fix any issues before they escalate into bigger problems.
Encrypt Your Data

Encryption is your best friend when it comes to data security. Ensure that all data passing through your proxy server is encrypted. This practice makes it extremely difficult for hackers to decipher any information they might intercept. Using SSL encryption for your website and any online platforms your business operates is a smart move. Here’s why encryption matters:
- Protects Data in Transit: Encryption secures your data as it travels between your server and your users’ devices, safeguarding sensitive information from eavesdroppers.
- Boosts Customer Confidence: When customers know their data is encrypted, their trust in your business increases, enhancing your brand’s reputation.
- Compliance and Regulation: Many industries have regulations requiring the encryption of sensitive data. Staying compliant not only protects your customers but also shields your business from legal repercussions.
Implementing encryption across all your online activities ensures that your business’s and customers’ data remains confidential and secure.
Educate Your Team on Safe Online Practices
When it comes to beefing up your proxy’s defense line, getting your team savvy about safe online habits is a game-changer. After all, the know-how to dodge cyber sneak attacks—like those tricky phishing attempts or malware—is as crucial as the tech itself. Here’s the rundown on the essential tips to drill into your team:
- Recognize and Report Phishing Attempts: Train your employees to identify signs of phishing emails, such as urgent language, misspellings, or requests for sensitive information. Encourage them to report any suspicious emails to the IT department.
- Use Strong Passwords: Emphasize the importance of using strong, unique passwords for all accounts and changing them regularly. Consider implementing a company-wide password manager to simplify this process.
- Avoid Public Wi-Fi for Work-Related Tasks: Public Wi-Fi networks are not secure. Teach your team to use a secure, company-provided VPN when accessing work resources from public networks.
Turning your team into cyber-savvy defenders amps up your proxy protection and keeps the digital fort secure.
Monitor and Analyze Proxy Logs
Proxy logs are a goldmine of information about your network’s security. By monitoring and analyzing these logs, you can identify suspicious activities and take immediate action. Look out for unusual patterns, such as repeated attempts to access certain resources or large data transfers. These could be signs of a security breach or an ongoing attack.
Leverage Advanced Proxy Features
To maximize your data security, don’t shy away from exploring advanced features offered by proxy servers. These features are designed to tailor security measures to fit your specific business needs, providing a more personalized and robust defense system. Here are some advanced features to consider:
- Rate Limiting: This feature helps prevent denial-of-service attacks by limiting the number of requests a user can make to your server within a certain time frame. By setting sensible thresholds, you can ensure your resources remain available for legitimate users.
- IP Whitelisting: By creating a whitelist of approved IP addresses, you can ensure that only trusted devices can access your network. This is particularly useful for businesses that operate in a fixed location or have employees who work remotely from secure locations.
- Access Controls: Customize who can see what by setting up detailed access controls. This means you can restrict access to sensitive data based on user roles, ensuring that only authorized personnel can view critical information.
- Content Filtering: Use your proxy server to filter out harmful or unwanted content before it reaches your network. This not only improves security but can also increase productivity by blocking access to non-work-related sites.
- SSL Inspection: With SSL inspection, your proxy can decrypt, inspect, and re-encrypt SSL-encrypted traffic. This allows you to identify and block threats hidden in encrypted traffic, a common tactic used by attackers to bypass security measures.
Incorporating these advanced features into your proxy setup can significantly enhance your organization’s online security posture. By doing so, you’re not just defending your data; you’re creating a more efficient and controlled online environment for your business operations.
Stay Informed About Latest Security Threats
The cyber security landscape is always evolving, with new threats emerging regularly. Stay informed about the latest security threats and trends. This knowledge allows you to adapt your proxy setup and overall security strategy, keeping your business one step ahead of potential attackers.
Conclusion
Proxies offer a powerful tool for businesses aiming to protect themselves in the digital world. From masking IP addresses to facilitating data scraping and competitive intelligence gathering, proxies can be a valuable asset in your cybersecurity strategy. By understanding the different types of proxies and implementing them securely, you can create a more robust online defense for your business and its sensitive data.